-
Notifications
You must be signed in to change notification settings - Fork 588
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
--overlay-named exits with error as of linux 5.1.15 (overlayfs) #2799
Comments
|
I think --rbind might be able to work around this. |
|
Fix for docker: moby/moby@477bf1e |
|
Maybe I don't fully understand the docker fix, but I wonder a bit what's the point of an overlay just to make the file system read-only. @netblue30 do you have an idea regarding the way forward? |
Or maybe it could serve as a simple switch for apps that really don't need to write anything at all. |
|
There is some kernel fix available in Linux 5.3.1 and 5.2.17, @lskrejci could you try if you can still reproduce issue no those kernels? |
|
Still fails on Linux 5.2.17 so some firejail changes are still needed: |
|
The same problem happens with the latest Linux kernel update in Debian Buster. With the previous 4.19.0-5 kernel Firejail works fine with the overlay feature, but when you upgrade to 4.19.0-6 you get the same "fs_overlayfs: Too many levels of symbolic links" error |
|
I guess debian backported upstream patches as they were security related. |
|
I have the same problem (at least I think that it's the same) and some logs: and: Kernel 4.19.79-1-MANJARO x86_64. |
|
For now, I ended up disabling --overlay feature for kernels 4.19 and newer. I am getting "fs_overlayfs: Too many levels of symbolic links" on debian stable, kernel 4.19. |
|
I recall testing and finding that mount --rbind did fix the issue. I can't quite recall what I bind mounted though. |
|
I think it's a similar trick to making pivot_root works, you do |
|
thanks, I'll try it out! |
|
Distribution: Arch Linux |
|
@springzfx OP use the same firejail version. There is a release coming, see release-0.9.62 branch. |
|
This still happens, any fixes in sight? Any viable workaround? |
|
Instead of waiting for kernel fixes related to this, could it be worked around by having firejail use: |
|
@netblue30 Is there any planned fix or known workaround for this issue? It was one of my favorite things about this project. |
|
took another look at the issue. I think the kernel is valid to reject this mount. if you do then, patch firejail to use |
|
@netblue30 where are you? this has been broken for over a year now, ridiculous, new profiles are less important than fixing this |
|
Are there no workarounds for this for now? |
|
Another workaround has been suggested in: https://bugs.debian.org/971578 |
|
Wish a fix. Thanks all developers 👍 :) |
same here |
|
@netblue30 Any news on this? I too like the suggested alternative of using |
Since users are still asking about it. Relates to netblue30#2799 netblue30#4178.
Since users are still asking about it. Relates to netblue30#2799 netblue30#4178.
Since users are still asking about it (see netblue30#6631). Relates to netblue30#2799 netblue30#4178.
|
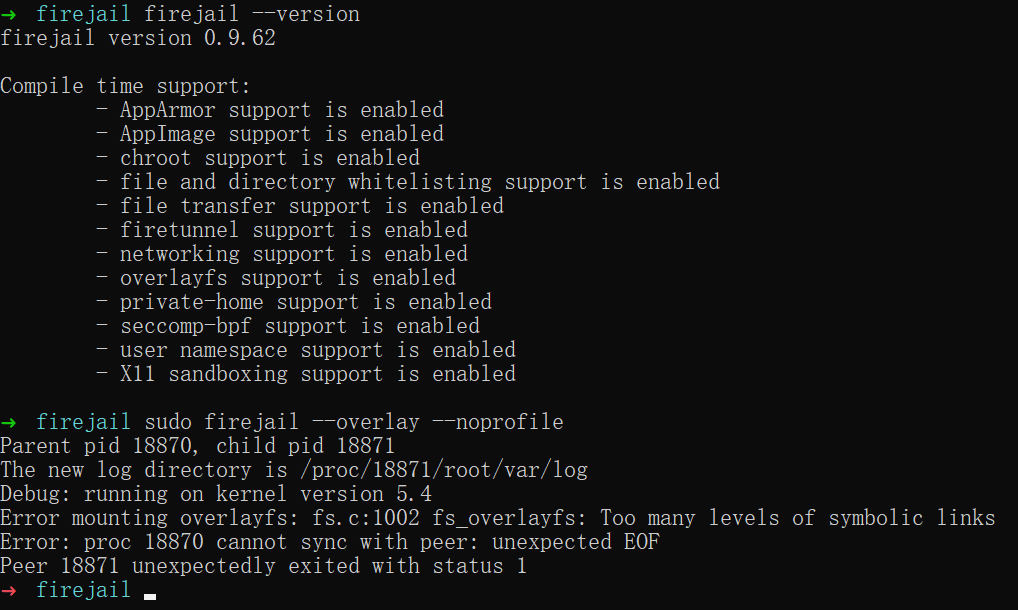
Running
firejail --noprofile --overlay-named=testfails:dmesg on both system configurations contains:
The same command works on linux 5.1.14.
Upstream commit that appears to have introduced the issue: ovl: detect overlapping layers
Environment:
Relates to:
The text was updated successfully, but these errors were encountered: