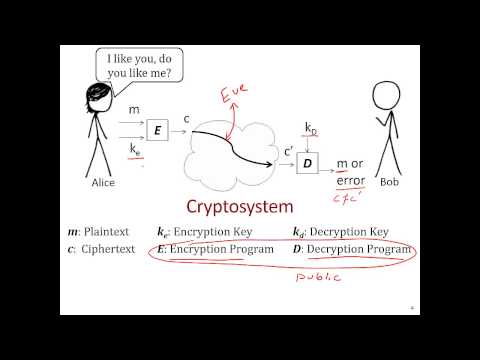
Remember when we set up SSH keys to set up a secure connection between GitHub and your local machine so that it doesn't ask you for your password every time you run git pull? That was an example of encryption, specifically asymmetric encryption.
This is your public key
cat ~/.ssh/id_rsa.pub
This is your private key
cat ~/.ssh/id_rsa
A brief aside...
A system with a public and private key is known as asymmetric encrpytion, or private key encryption. Check out this video from David Brumly at Carnegie Mellon University for a quick overview of the basics of cryptography.
- Share our public key to securely communicate with GitHub (or other services).
- Use someone else's public key to encrypt and send a message only they can read.
- Encrypt or sign a document with your private key to prove that it originated with you (anyone can use your public key to decrypt, or verify your signature)
- Remotely login into another computer with a program known as secure shell (
ssh). - Copy a file securely from another computer using secure copy (
scp). - Lots of other things....
Yeah, its a really powerful tool that doesn't require a geeky genius to use.
-
Encrypting Files: https://bjornjohansen.no/encrypt-file-using-ssh-key
-
HTTPS (We'll cover this more in a later lesson)
-
Cryptocurrency: https://walletgenerator.net/
-
Chat (Signal, WhatsApp, Ketbase etc... are end-to-end encrypted chat platforms)
-
Digital Signatures: https://us-cert.cisa.gov/ncas/tips/ST04-018
-
Voting (in Estonia, at least): https://www.youtube.com/watch?v=GuKiJKL4WdI
-
Identification https://www.youtube.com/watch?v=9POUIiyhowk
Check out this video about all of the digital services Estnoia has been able to provide by issuing a public/private key pair to each citizen:
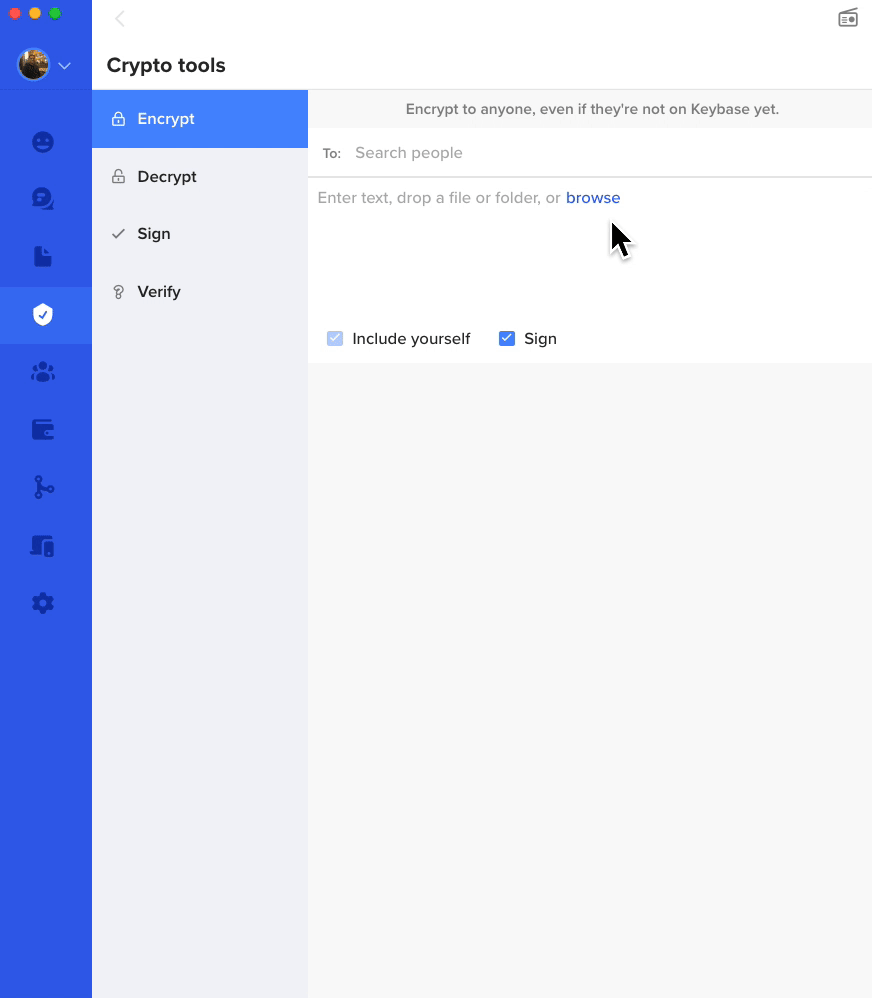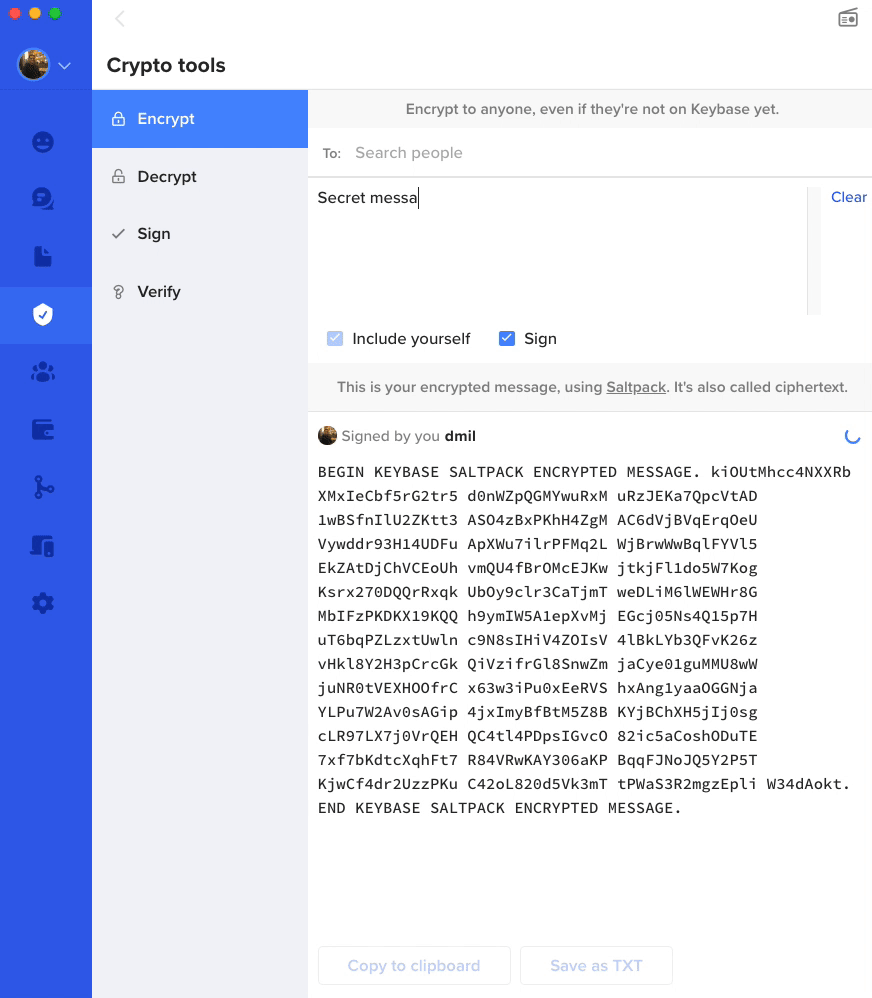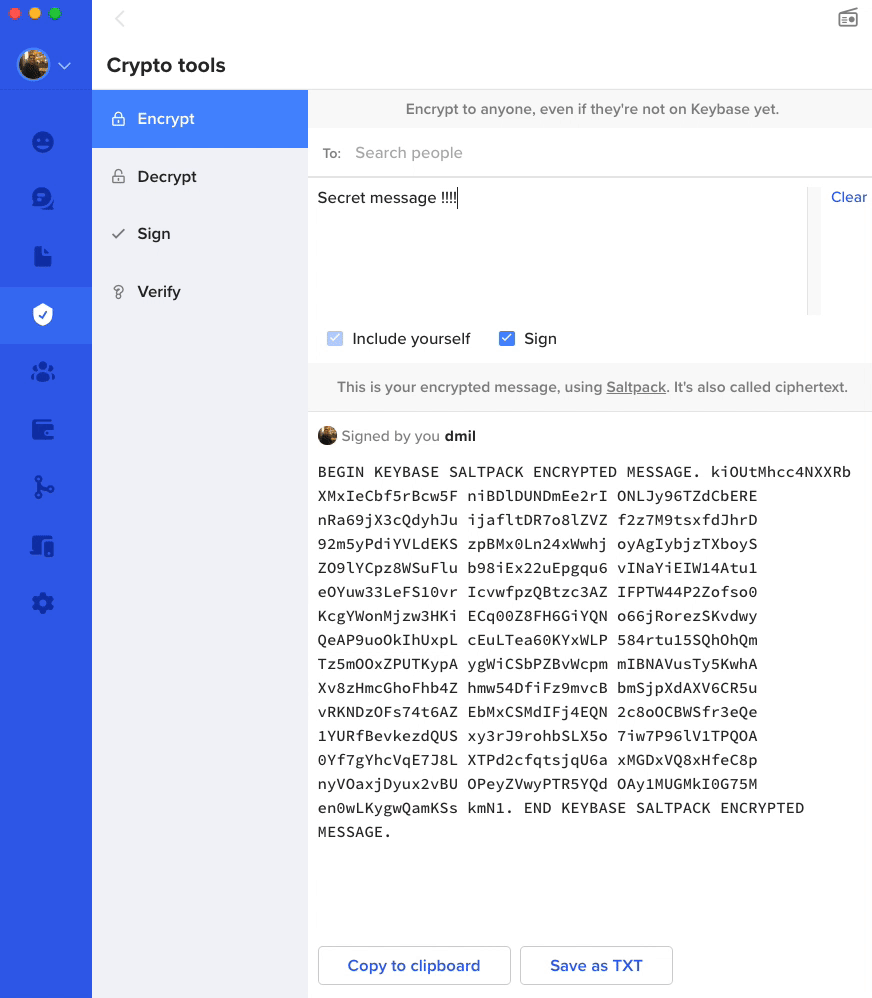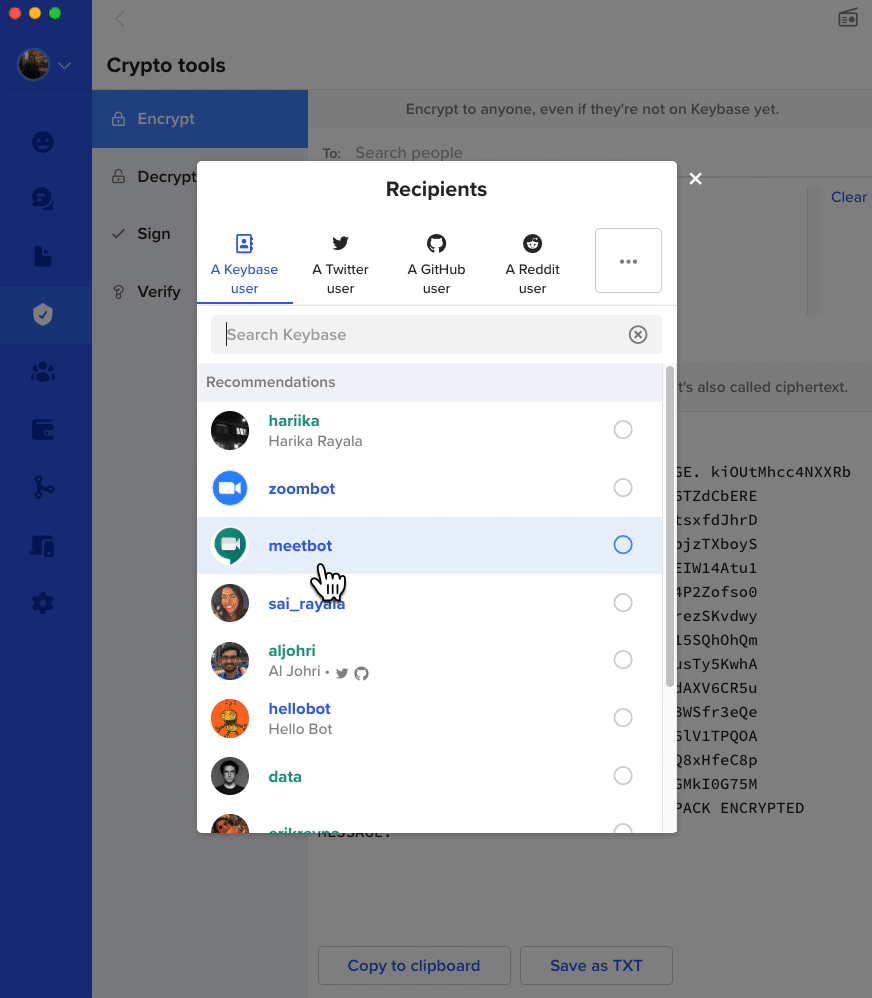
Finally, if you want to play around more with encryption, I'd highly reccomend Keybase. Keybase allows you to encrpyt messages as you can see in the gif below using someone else's public key. Then, you can send that message to them over any public medium and ONLY they can read it. You can also encrypt a message with multiple keys. Keybase has a lot of other great features including secure chat, idenity verification, file transfer, and more. I would encourage you to play around with it and learn more and really bring the idea of public and private keys to life!
Later in class, if there is time, we will learn how to send each other encrypted messages using the SSH keys we just created today! (modules/security/encryption.md)
The math behind Cryptography has something to do with finding the factors of really large prime numbers. This article on arstechnica provides a great rundown! https://arstechnica.com/information-technology/2013/02/lock-robster-keeping-the-bad-guys-out-with-asymmetric-encryption/
Click on this link for the encryption assignment: https://classroom.github.com/a/CUy9NKP_
Lot of thorny policy issues related to:
- proposals to restrict encryption
- install backdoors
- law enforcement investigations
- Check out https://keybase.io/
- Prime numbers and whatnot: https://arstechnica.com/information-technology/2013/02/lock-robster-keeping-the-bad-guys-out-with-asymmetric-encryption/
Discuss with your classmates in the #encryption channel in Slack! If I'm around, I can chime in too. Or ask me during class!