-
Notifications
You must be signed in to change notification settings - Fork 4k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
feat(pipes-alpha): support for customer-managed KMS keys to encrypt pipe data #33546
Conversation
| @@ -23,7 +23,7 @@ can be filtered, transformed and enriched. | |||
|
|
|||
| 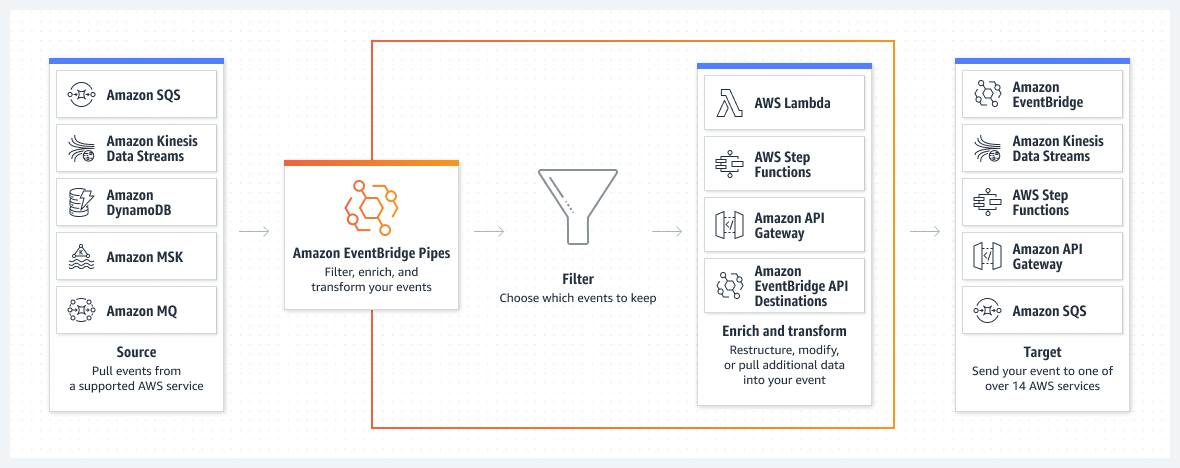 | |||
|
|
|||
| For more details see the [service documentation](https://docs.aws.amazon.com/eventbridge/latest/userguide/eb-pipes.html). | |||
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Removed several unnecessary spaces.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
(This review is outdated)
Codecov ReportAll modified and coverable lines are covered by tests ✅
Additional details and impacted files@@ Coverage Diff @@
## main #33546 +/- ##
=======================================
Coverage 82.21% 82.21%
=======================================
Files 119 119
Lines 6876 6876
Branches 1162 1162
=======================================
Hits 5653 5653
Misses 1120 1120
Partials 103 103
Flags with carried forward coverage won't be shown. Click here to find out more.
|
✅ Updated pull request passes all PRLinter validations. Dismissing previous PRLinter review.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Thanks for your contribution! I think it's mostly fine.
I've added one question.
Also, I previously opened an issue here: #31453.
Would it be possible to link this contribution to that issue?
| @@ -295,6 +303,7 @@ export class Pipe extends PipeBase { | |||
| targetParameters: target.targetParameters, | |||
| desiredState: props.desiredState, | |||
| logConfiguration: logConfiguration, | |||
| kmsKeyIdentifier: props.kmsKey?.keyArn, | |||
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Just a question—did it work correctly even without setting a key policy?
When I previously attempted to contribute to this, I encountered an error without a key policy, but I couldn't come up with a proper way to configure it and had to give up at the time.
It might have been my misunderstanding back then, or something might have changed with an update. If it worked fine, please just ignore this question.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
You are absolutely right.. I misunderstood that this implementation would be work fine. Thank you for your great suggestion.
How about adding the restriction that makes pipeName mandatory when kmsKey is provided?
This idea is not ideal, but it would provide the minimum feature that enables us to configure CMK for Pipes.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Thank you for confirming. So that's how it is...
I think your suggested solution is good.
Personally, I've been considering the following three options:
- Make name mandatory when kmsKey is specified. This is the same as the suggestion you provided.
- Instead of setting name to undefined when it's not specified, automatically generate it using Names.uniquid. However, I understand this would be a breaking change.
- Configure kmsKey using a custom resource. I think this option is not ideal.
Based on the above, I believe option 1 or option 2 would be good, and I think option 1 would be better to avoid a breaking change.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I hadn't thought of option 2. I think implementing option 2 with a feature flag is also a good idea.
For now, I'll proceed with option 1. Of course, I'll also add integration testing to verify the functionality.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I've just noticed that the feature flag is not essential because this is alpha module..
I think the option 2 might be preferable for alpha module. I'll leave the decision to the maintainer.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I also think Options2 is smarter, but since the impact is significant, I'd like to wait for the maintainer's opinion.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Thanks for the deep dive. I think Option 1 makes sense to me. Can you help me understand Option 2 + feature flag solution?
In my understanding, we can't create the policy without knowing the pipe name. If we add a feature flag, for new stacks, we will always create a default pipe name if not specified which would solve the issue. However, for existing stack (who did not enable this feature flag), we will still have the same issue right?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Thank you for the clarification.
However, for existing stack (who did not enable this feature flag), we will still have the same issue right?
You're absolutely right! When setting a CMK for stacks under an App where the function flag is not enabled, the pipeName cannot be obtained, resulting in the inability to set the correct key policy.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Thanks for the quick response. Given the above discussion, I'll remove the do-not-merge label and let's go with the solution you had here. Thank you!
|
@mazyu36 Thank you for your nice review!! I've addressed your comments. |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Thanks! LGTM
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Great, thank you!
| @@ -295,6 +303,7 @@ export class Pipe extends PipeBase { | |||
| targetParameters: target.targetParameters, | |||
| desiredState: props.desiredState, | |||
| logConfiguration: logConfiguration, | |||
| kmsKeyIdentifier: props.kmsKey?.keyArn, | |||
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Thanks for the deep dive. I think Option 1 makes sense to me. Can you help me understand Option 2 + feature flag solution?
In my understanding, we can't create the policy without knowing the pipe name. If we add a feature flag, for new stacks, we will always create a default pipe name if not specified which would solve the issue. However, for existing stack (who did not enable this feature flag), we will still have the same issue right?
|
Adding a |
|
Thank you for contributing! Your pull request will be updated from main and then merged automatically (do not update manually, and be sure to allow changes to be pushed to your fork). |
AWS CodeBuild CI Report
Powered by github-codebuild-logs, available on the AWS Serverless Application Repository |
|
Thank you for contributing! Your pull request will be updated from main and then merged automatically (do not update manually, and be sure to allow changes to be pushed to your fork). |
|
Comments on closed issues and PRs are hard for our team to see. |
Issue # (if applicable)
Closes #31453
Reason for this change
AWS Pipes supports for encrypting data by customer managed KMS key instead of Amazon managed key.
https://docs.aws.amazon.com/eventbridge/latest/userguide/eb-encryption-pipes-cmkey.html
The L2 Pipe construct does not support this feature now.
Description of changes
kmsKeyprop toPipePropsDescribe any new or updated permissions being added
https://docs.aws.amazon.com/eventbridge/latest/userguide/eb-encryption-key-policy.html#eb-encryption-key-policy-pipe
Description of how you validated changes
Add both unit and integ tests.
Checklist
By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license