This repository contains various threat model examples for different technologies and systems. These resources provide illustrative examples of threat models across different domains, helping security professionals, developers, and researchers better understand how threat modeling can be applied effectively to address security risks.
This project was established to give an idea of how the end results of a threat model might look like. With so many guidelines and methodologies available, we noticed that having concrete examples would help the community better understand what 'good' looks like.
-
OAuth 2.0
-
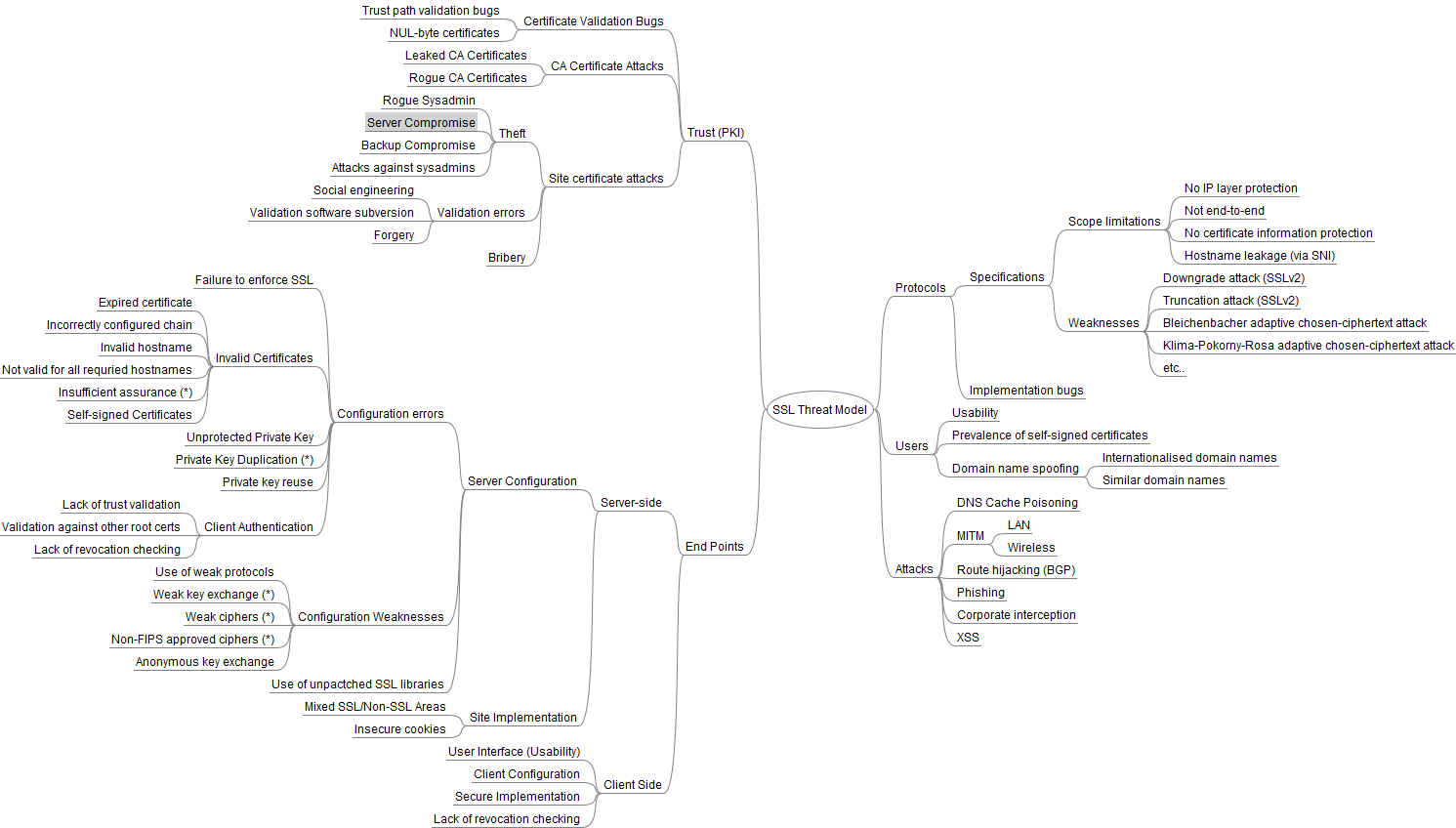
SSL
-
DNSSEC, DoT, and DoH
-
Web Application
Cloud and container environments are essential for scalable infrastructure but are also prime targets for attacks. The following examples showcase key threat models in these areas.
-
Kubernetes
-
Docker
-
AWS Fargate
-
Amazon S3
-
Google Cloud Storage
Mobile and IoT devices are integral to modern systems, but they introduce unique security challenges. These examples demonstrate approaches to mitigate such risks.
-
Mobile Applications
-
IoT Authentication
-
IoT Devices
-
Smart Home
-
IoT Supply Chain
AI systems are becoming increasingly integrated into critical operations. The following example explores threat modeling for generative AI workloads.
- Generative AI Workload
-
PCI DSS
-
Password Storage Module (PSM)
-
Certificate Transparency
-
Account Takeover (ATO)
-
Password Managers
📢 Contributing
We welcome contributions from the community! Open a pull request to share your expertise.
📝 License
This repository is licensed under the MIT License. See the LICENSE file for more details.