-
Notifications
You must be signed in to change notification settings - Fork 370
Setting up Metasploit RPC Connection
The Metasploit RPC allows you to display hosts and vulnerabilities from the Metasploit database within Serpico. Once setup, you can automatically map vulnerabilities from a workspace into your Serpico report.
-
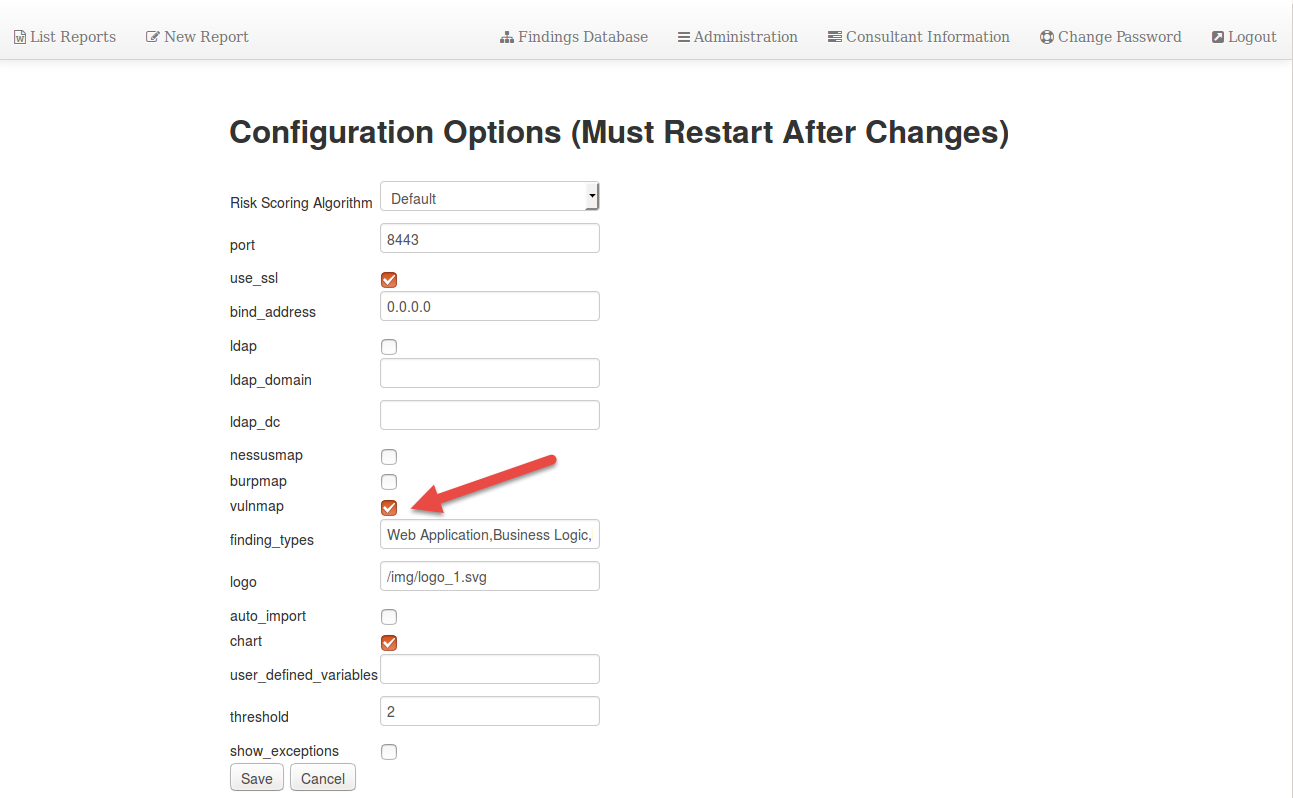
Log in as an Administrator, Under the "Maintenance Menu" on the Left hand side of the screen, select "Modify Configuration"
-
Check the box labeled "vulnmap" and click "save".
-
Restart Serpico for changes to apply.
-
On the system you have Metasploit installed on, issue the following command to start the Metasploit RPC service:
sudo msfrpcd -U msfuser -P msfchangeme --ssl
For additional information or troublshooting, see the following wiki page: https://github.com/rapid7/metasploit-framework/wiki
You must have MSF RPC working before moving on.
-
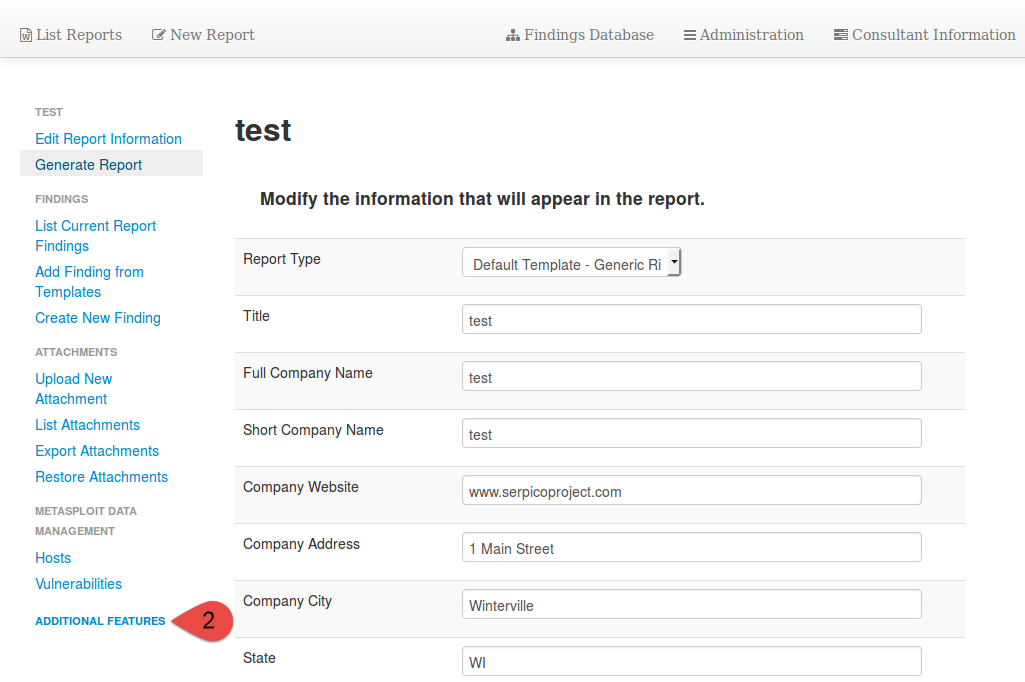
Next access the report for which you want to configure the Metasploit RPC connector for.

-
On the Left hand side select "Additional Features"
-
Under Additional Features select "Configure a Metasploit RPC Connection"

-
Configure Metasploit RPC Settings:

-
To test the Metasploit connection, select "Hosts" under "Metasploit Data management" menu on the left (when editing a report). If hosts exist in your workspace, they will be displayed in Serpico. If you get an error, double check that Serpico can communicate with the msfrpcd listener.

Example of hosts information:

Example of vuln information:

Each Serpico finding you want anatomically mapped will have to have a CVE (or other supported ID) assigned to the finding. This is done by editing the finding in the findings database. More information on what IDs are supported can be found by clicking on the "Add new vuln mapping ID" button:

Once mappings exist, if your Metasploit workspace contains a vulnerability matching the mapping, the finding will be automatically added.
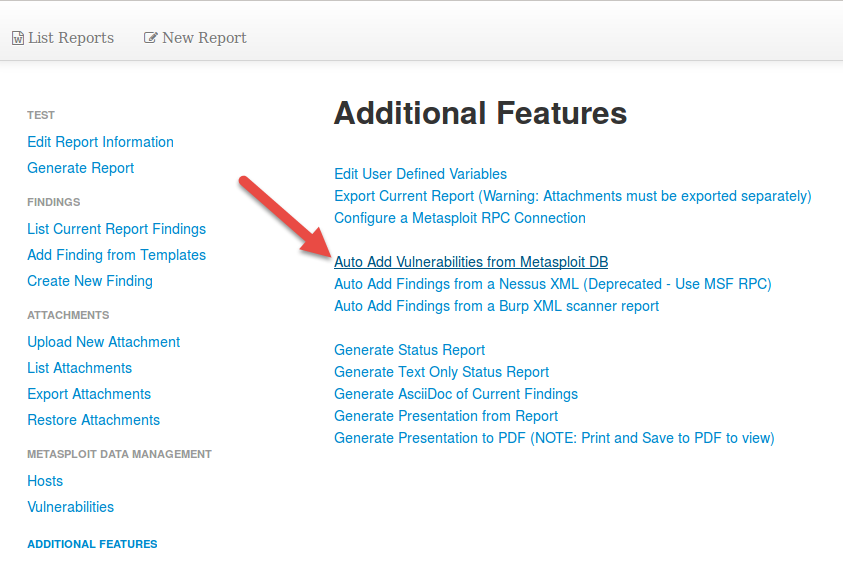
To automatically map findings, edit a report that has a Metasploit connection, then choose "Additional Features", and select "Auto Add Vulnerabilities from Metasploit DB":
- msfprcd without SSL is NOT supported. You must need the --ssl when starting msfrpc.
- Do not use "load msgrpc", instead launch via the command line tool msfrpcd
- Use only supported Ruby versions. (currently 2.1.5, other versions have been known to break msf rpc functionality)
- Before submitting an issue, make sure you have verified traffic with tcpdump/wireshark, and confirm your Ruby version.